What is the Method To Use System Optimizer in Webroot?
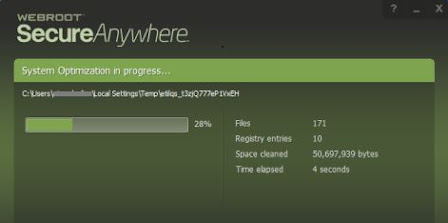
Webroot antivirus is the astonishing security item which shields your information from arising danger and can be handily introduced through Webroot.com/safe. In this blog, you will peruse the strategy to utilize framework enhancer in Webroot. Change System Optimizer Setting: On the off chance that the client needs to change System Optimizer settings, you need to twofold tap on the Webroot symbol. Here, the fundamental interface shows and afterward you should tap on Advanced Settings. Presently, the Settings window concocts the Install Settings sub-sheet dynamic. Now, you need to choose System Optimizer. You will see the System Optimizer sheet on your screen. Then, select or deselect any of the accompanying alternatives:. Clipboard substance Windows Temporary Folder Framework Temporary organizer Windows Update Temporary organizer Windows Registry Streams Default logon client history Memory dump documents Compact disc copying stockpiling organizer Streak Cookies Reuse Bin Lat